 PDF(1062 KB)
PDF(1062 KB)


 PDF(1062 KB)
PDF(1062 KB)
 PDF(1062 KB)
PDF(1062 KB)
基于科研过程的科学数据安全行为研究
Research on Scientific Data Security Behavior Based on Scientific Research Process
 ,
,

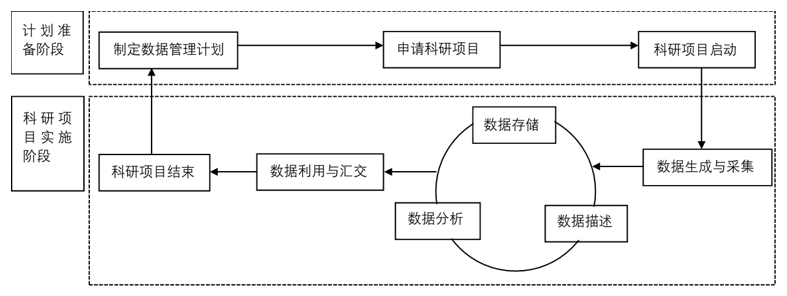
[目的/意义] 通过界定科学数据安全行为的概念,分析科研活动不同阶段应如何保证科学数据安全,对规范科研人员的科学数据安全行为、促进科学数据安全管理、制定科学数据安全政策、完善科学数据安全管理体系具有重要意义。[方法/过程] 采用网络调研法,整合信息安全行为和科学数据安全管理的定义,提出科学数据安全行为的概念。在此基础上,从理论出发,结合科学数据管理与共享的实践经验,系统阐述如何通过个人行为保障科学数据安全。[结果/结论] 现阶段科学数据安全管理主要针对科学数据管理平台,从行为学视角探讨科学数据安全的研究尚处于起步阶段。本文基于科研过程,从两方面对如何规范科研人员的行为以提升科学数据安全进行分析:其一,对存在科学数据安全风险的阶段,结合科学数据管理的政策对此提出针对性的改进策略;其二,对不存在明显安全风险的阶段,根据国内外科学数据管理的实践经验,提出建议。
[Purpose/significance] This paper defines the concept of scientific data security behavior, and combines different stages of research activities to analyze how to ensure the safety of scientific data in the scientific research process. It is of great significance to standardize the scientific data security behavior of scientific researchers, promote scientific data security management, formulate scientific data security policies, and improve the scientific data security management system. [Method/process] The network research method was adopted to integrate the definition of information security behavior and scientific data security management, and then, the concept of scientific data security behavior was proposed. On this basis, starting from the theory, this paper combined with the practical experience of scientific data management and sharing to explained that way to ensure the security of scientific data through personal behavior. [Result/conclusion] At this stage, scientific data security management is aimed at scientific data management platform. Research on scientific data security from the perspective of behavior is still in its infancy. Based on the scientific research process, this paper analyzes how to standardize the behavior of scientific researchers to improve the security of scientific data from two aspects. First, in the stage which existence of scientific data security risk, combined with the policy of scientific data management, this paper proposes a targeted improvement strategy. Second, for the stage where there is no obvious security risk, suggestions are put forward which based on the practical experience of scientific data management at home and abroad.
科学数据安全行为 / 科学数据 / 信息安全行为 / 科学数据管理
scientific data security behavior / scientific data / information security behavior / scientific data management
| [1] |
中国科学院.第四届(2017)科学数据大会会议通知.[EB/OL].[2018-10-20].http://www.cas.cn/xs/201707/t20170711_4608195.shtml.
|
| [2] |
中华人民共和国中央人民政府.科学数据是重要战略资源[EB/OL].[2018-11-24].http://www.gov.cn/zhengce/2018-04/06/content_5280211.htm.
|
| [3] |
黄如花,王斌,周志峰.促进我国科学数据共享的对策[J].图书馆,2014(3):7-13.
|
| [4] |
World Data System. Data sharing principles[EB/OL].[2018-10-08].https://www.icsu-wds.org/.
|
| [5] |
Australian National Data Service. Research data Australian[EB/OL].[2018-10-08].https://www.ands.org.au/.
|
| [6] |
Digital Curation Centre[EB/OL].[2018-10-08].http://www.dcc.ac.uk/.
|
| [7] |
The University of Edinburgh. Research resources[EB/OL].[2018-10-08].https://www.ed.ac.uk/information-services/library-museum-gallery/crc/research-resources.
|
| [8] |
Princeton University. Research data security[EB/OL].[2018-10-10].https://ria.princeton.edu/research-data-security.
|
| [9] |
中华人民共和国人民政府.国务院办公厅关于印发科学数据管理办法的通知[EB/OL].[2018-08-12].http://www.gov.cn/zhengce/content/2018-04/02/content_5279272.htm.
|
| [10] |
The Stationery Office. Data Protection Act 1998[EB/OL].[2018-10-10].http://www.legislation.gov.uk/ukpga/1998/29/pdfs/ukpga_19980029_en.pdf.
|
| [11] |
BBSRC.BBSRC data sharing policy[EB/OL].[2018-04-18].http://www.bbsrc.ac.uk/documents/data-sharing-policy-pdf/.
|
| [12] |
Health Information Privacy. Summary of the HIPAA security rule[EB/OL].[2018-10-20].https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html.
|
| [13] |
Research Ethics and Compliance. Data security guidelines[EB/OL].[2018-10-20].https://research-compliance.umich.edu/data-security-guidelines.
|
| [14] |
IDG—Insights Intent and Engagement.2018 Global state of information security survey[EB/OL].[2018-12-02].https://www.idg.com/tools-for-marketers/2018-global-state-information-security-survey/.
|
| [15] |
Joint Information Systems Committee. Security of research data[EB/OL].[2018-10-10].https://www.jisc.ac.uk/guides/data-protection-and-research-data/security-of-research-data.
|
| [16] |
Euronews. The Facebook data leak:what happened and what's next[EB/OL].[2018-10-12].https://www.euronews.com/2018/04/09/the-facebook-data-leak-what-happened-and-what-s-next.
|
| [17] |
中华人民共和国中央人民政府.科学数据,如何科学管理[EB/OL].[2018-08-29].http://www.gov.cn/zhengce/2018-04/08/content_5280429.htm.
|
| [18] |
刘桂锋,魏悦,钱锦琳.高校科研数据管理与共享政策的案例与执行模型研究[J].图书馆论坛,2018,38(11):27-34.
|
| [19] |
曾忠平,杨哲,刘春梅.用户信息安全行为研究述评[J].情报杂志,2014,33(12):184-188.
|
| [20] |
李晶.信息安全行为研究现状与发展动态述评[J].图书情报工作,2014,58(24):126-130.
|
| [21] |
WOOD C C, BANKS JR W W. Human error: an overlooked but significant information security problem[J].Computers and security,1993,12 (1):51-60.
|
| [22] |
MCCAULEY-BELL P R, CRUMPTON L L. The human factors issues in information security: what are they and do they matter[C]//Proceedings of the human factors and ergonomics society annual meeting. Los angeles: Sage publications,1998:439-443.
|
| [23] |
ANDERSON C L, AGARWAL R. Practicing safe computing: a multimedia empirical examination of home computer user security behavioral intentions[J]. Management information systems quarterly,2010,34 (3):613-643.
|
| [24] |
SCHULTZ E. The human factor in security[J]. Computers and security,2005,24 (6):425-426.
|
| [25] |
STANTON J M, CALDERA C,GUZMAN I, et al. Behavioral information security: an overview, research agenda, and preliminary results[C]//The security conference. Las vegas: Nevada,2003:23-24.
|
| [26] |
DZAZALI S, SULAIMAN A, ZOLAIT A H. Information security landscape and maturity level: case study of Malaysian Public Service (MPS) organizations[J].Government information quarterly,2009,26 (4):584-593.
|
| [27] |
LIANG H, XUE Y. Understanding security behaviors in personal computer usage: a threat avoidance perspective[J].Journal of the Association for Information Systems,2010,11 (7):394-413.
|
| [28] |
WIRTZ J, LWIN M O, WILLIAMS J D. Causes and consequences of consumer online privacy concern[J].International journal of service industry management,2007,18 (4):326-348.
|
| [29] |
黄鑫,邓仲华.数据密集型科学研究的需求分析与保障[J].情报理论与实践,2017,40(2): 66-70.
|
| [30] |
赵华,朱亮,鲜国建,等.数据监护现状分析及对我国农业科学数据监护的启示[J].数字图书馆论坛,2017(11):9-14.
|
| [31] |
沈怡.科研数据实践的实证研究对数据管理和共享的重要意义:个案回顾、反思与前瞻[J].图书情报知识,2018(4):102-108.
|
| [32] |
LEE D J, STVILIA B. Practices of research data curation in institutional repositories: a qualitative view from repository staff[J].PLOS ONE,2017,12 (3):1-44.
|
| [33] |
The Digital Curation Centre. What is digital curation?[EB/OL].[2018-11-12].http://www.dcc.ac.uk/digital-curation/what-digital-curation.
|
| [34] |
吴金红,陈勇跃.面向科研第四范式的科学数据监管体系研究[J].图书情报工作,2015,59 (16):11-17.
|
| [35] |
宋筱璇,王延飞,钟灿涛.国内外科研数据安全管理政策比较研究[J].情报理论与实践, 2016,39 (11):10-16.
|
| [36] |
丁培.国外大学科研数据管理政策研究[J].图书馆论坛,2014,34 (5):99-106.
|
| [37] |
张瑶,顾立平,杨云秀,等.国外科研资助机构数据政策的调研与分析——以英美研究理事会为例[J].图书情报工作,2015,59 (6):53-60.
|
| [38] |
郝世博,徐文哲,唐正韵.科学数据共享区块链模型及实现机理研究[J].情报理论与实践, 2018(11):57-62.
|
| [39] |
司莉,邢文明.国外科学数据管理与共享政策调查及对我国的启示[J].情报资料工作, 2013(1):61-66.
|
| [40] |
马海群,蒲攀.国内外开放数据政策研究现状分析及我国研究动向研判[J].中国图书馆学报,2015,41(5):76-86.
|
| [41] |
LISCOUSKI J. The Data Librarian: introducing the Data Librarian[J].Journal of analytical methods in chemistry,1900,19 (6):199-204.
|
| [42] |
CREAMER A, MORALES M E, CRESPO J, et al. An assessment of needed competencies to promote the data curation and management librarianship of health sciences and science and technology librarians in New England[J]. Journal of eScience librarianship,2012,1 (1):4.
|
| [43] |
KHAN H R, DU Y. What is a data librarian?: A content analysis of job advertisements for data librarians in the United States Academic Libraries[J]. International federation of library associations and institutions, 2018(7):1-9.
|
| [44] |
MARTIN E R. Highlighting the informationist as a data librarian embedded in a research team[J].Journal of eScience librarianship,2013,2 (1):1-3.
|
| [45] |
胡绍君.面向科研数据管理的高校学科馆员能力建设研究[J].图书情报工作, 2016,60(22):74-81.
|
| [46] |
Harvard University. Harvard research data security policy[EB/OL].[2019-05-16]. https://vpr.harvard.edu/pages/harvard-research-data-security-policy.
|
| [47] |
Princeton University. Research data security[EB/OL].[2019-05-16]. https://ria.princeton.edu/research-data-security.
|
| [48] |
Stanford Medicine. Research and security[EB/OL].[2019-05-16]. https://med.stanford.edu/irt/security/research.html.
|
| [49] |
司莉,邢文明.科学数据管理与共享的理论与实践[M].武汉:武汉大学出版社,2017:81.
|
| [50] |
杨林,钱庆,吴思竹.科学数据管理生命周期模型比较[J].中华医学图书情报杂志,2016,25 (11):1-6.
|
| [51] |
尹春晓.高校科学数据管理嵌入式服务模式探索[J].情报资料工作,2017,38 (2):77-82.
|
| [52] |
杨传汶,徐坤.基于生命周期的动态科学数据服务模式研究[J].图书馆论坛,2015,35 (10): 82-87.
|
| [53] |
Nation Science Foundation. NSF data management plan requirements[EB/OL].[2018-10-23].https://www.nsf.gov/bfa/dias/policy/dmp.jsp.
|
| [54] |
Stanford Libraries. Data management plans[EB/OL].[2018-09-01].https://library.stanford.edu/research/data-management-services/data-management-plans.
|
| [55] |
黄国彬,邸弘阳,张莎莎,等.数据管理计划工具DMPTool的服务体系剖析[J].图书情报工作,2018,62(4):37-43.
|
| [56] |
王海彪,卫军朝.科学数据管理关键因素研究——基于爱丁堡大学科学数据管理实践及启示[J].图书馆杂志,2017,36(1):20-26.
|
| [57] |
Digital Curation Centre.DMPonline[EB/OL].[2018-08-13].https://dmponline.dcc.ac.uk/.
|
| [58] |
University of California Curation Center. DMPTool[EB/OL].[2018-11-10].https://dmptool.org/.
|
| [59] |
MIT Libraries. Write a data management plan[EB/OL].[2018-11-12].https://libraries.mit.edu/data-management/plan/write/.
|
| [60] |
Stanford Libraries. About data management plans (DMPs)[EB/OL].[2018-11-12].https://library.stanford.edu/research/data-management-services/data-management-plans.
|
| [61] |
Medical Research Council. What is a data management plan?[EB/OL].[2018-11-12].https://mrc.ukri.org/documents/pdf/what-is-a-data-management-plan/.
|
| [62] |
KNATTERUD G L, ROCKHOLD F W, GEORGE S L, et al. Guidelines for quality assurance in multicenter trials: a position paper[J]. Controlled clinical trials,1998,19 (5):477-493.
|
| [63] |
DENSCOMBE M.怎样做好一项研究:小规模社会研究指南[M].陶保平,译. 上海:上海教育出版社,2011:115-119.
|
| [64] |
Northern Llinois University. Data collection[EB/OL].[2018-12-11].https://ori.hhs.gov/education/products/n_illinois_u/datamanagement/dctopic.html.
|
| [65] |
司莉, 封洁.科学数据的保存与维护:国际组织的动向[J].图书馆,2015(4):6-10.
|
| [66] |
Joint Information Systems Committee. Why preserve digital data?[EB/OL].[2018-08-21].http://www.dcc.ac.uk/digital-curation/why-preserve-digital-data.
|
| [67] |
谢春枝, 燕今伟.国内外高校科学数据管理和机制建设研究[J].图书情报工作,2013,57 (6):12-17.
|
| [68] |
Southampton Library. Research data management:file naming[EB/OL].[2018-12-01].http://library.soton.ac.uk/researchdata/filenaming.
|
| [69] |
UK Data Service. File names[EB/OL].[2018-12-01].https://www.ukdataservice.ac.uk/manage-data/format/organising.
|
| [70] |
University of Liverpool. Storing your research data[EB/OL].[2018-12-01].https://www.liverpool.ac.uk/library/research-data-management/storing-your-research-data/.
|
| [71] |
University of Concordia. Data storage and file formats[EB/OL].[2018-12-03].https://library.concordia.ca/help/data/data-storage.php.
|
| [72] |
The University Of Western Australia Research data preservation formats[EB/OL].[2018-12-03].http://guides.library.uwa.edu.au/c.php?g=325196&p=2178568.
|
| [73] |
Stanford Libraries. Best practices for file formats[EB/OL].[2018-12-04].https://library.stanford.edu/research/data-management-services/data-best-practices/best-practices-file-formats.
|
| [74] |
UK Data Service. Data backup[EB/OL].[2018-12-04]. https://www.ukdataservice.ac.uk/manage-data/store/backup.aspx.
|
| [75] |
Fordham University. Research data security guidelines[EB/OL].[2018-12-04]. https://www.fordham.edu/info/24327/guidelines_and_procedures/9959/research_data_security_guidelines/1.
|
| [76] |
Harvard University. Harvard research data security policy[EB/OL].[2018-12-05]. https://vpr.harvard.edu/pages/harvard-research-data-security-policy.
|
| [77] |
司莉,邢文明.科学数据管理与共享的理论与实践[M].武汉:武汉大学出版社,2017:60.
|
| [78] |
Southampton Library. Research data management:describing[EB/OL].[2018-12-05]. http://library.soton.ac.uk/researchdata/description.
|
| [79] |
涂志芳.科学数据出版生态系统与质量控制体系构建[J].图书与情报,2019(1):125-134.
|
| [80] |
WILKINSON M, DUMONTIER M, AALBERSBERG I. The FAIR guiding principles for scientific data management and stewardship[J].Scientific data,2016(3):167-172.
|
| [81] |
Oulun Yliopisto. Research data guide[EB/OL].[2018-12-04]. http://libguides.oulu.fi/Researchdata/Data_documentation.
|
| [82] |
The University of Western Australia. Metadata standards[EB/OL].[2018-12-04]. https://guides.library.uwa.edu.au/c.php?g=325196&p=2178564.
|
| [83] |
The Digital Curation Centre. List of metadata standards[EB/OL].[2018-12-04]. http://www.dcc.ac.uk/resources/metadata-standards/list.
|
| [84] |
司莉,邢文明.科学数据管理与共享的理论与实践[M].武汉: 武汉大学出版社,2017:61.
|
| [85] |
王卷乐,祝俊祥,杨雅萍,等.国外科技计划项目数据汇交政策及对我国的启示[J].中国科技资源导刊,2013(2):17-23.
|
| [86] |
国家重点基础研究发展计划资源环境领域项目数据汇交暂行办法[EB/OL]. [2018-12-08].http://www.973geodata.cn/files/1.pdf.
|
| [87] |
宋转玲,刘海行,葛人峰,等.国家自然科学基金委员会共享航次调查数据汇交体系构建[J].中国科学基金,2014,28(6):455-459.
|
| [88] |
国家科技基础条件平台.中医药科研课题数据汇交管理办法[EB/OL].[2018-12-10]. http://dbcenter.cintcm.com/content.jsp?id=189.
|
| [89] |
国家农业科学数据共享中心.农业科学数据汇交管理办法[EB/OL].[2018-12-10]. http://fishery.agridata.cn/ch_law.asp.
|
| [90] |
陕西省地政局.人工地震科学数据汇交与共享管理办法(试行)[EB/OL].[2018-12-10]. http://www.shxdzj.gov.cn/n1172/n1175/c532930/part/532931.pdf.
|
| [91] |
中国科学院南海海洋研究所.中国科学院南海海洋研究所数据汇交暂行办法[EB/OL]. [2018-12-08].http://odc.scsio.ac.cn/images/123.pdf.
|
| [92] |
国家材料科学数据共享网.材料科学数据提交格式规范[EB/OL].[2018-12-10]. http://matsec.ustb.edu.cn/uploadFiles/shujutijiao.pdf.
|
/
| 〈 |
|
〉 |